🦀 How Rust Crashed the Internet
Today’s issue: 2025 State of Rust Survey, GCC Supports Wild Linker, and C’s Sins No LLM Can Rust Away
Hello, Rustaceans
In this issue, we’ll discuss the recent outage at Cloudflare, present you a challenge, spotlight an amazing project, and share 10 incredible links of the week.
Here’s issue 94 for you!
A Message for You
Starting with the next issue (95), we’ll be pausing the challenges to give you a chance to participate in Advent of Code (AOC), running from December 1st to 15th.
We’ve set up a private leaderboard just for Rustaceans, join using the invite code: 5140157-18892126.
Expect no challenges from us during the AOC run.
MAIN NEWS
How Rust Crashed the Internet
If there’s anything we can learn from last week’s Cloudflare outage, which sidelined half the internet, it’s this: Rust’s unwrap() can be a disaster sometimes.
Cloudflare announced on September, 26 how they had recently rewritten ~20% of its edge network in Rust for better performance, security, and memory safety.
Fast forward to November 18, at 11:20 UTC (53 days later), a seemingly harmless DB permissions flip in Cloudflare’s ClickHouse cluster snowballed into their worst outage since 2019, serving HTTP 5xx error pages to users and halting traffic for core services like proxying, Workers KV, and blackholing sites from Shopify to Discord.
And the unlikely culprit? A cheeky little `unwrap()` in Rust code that said, “Nah, this can’t fail,” right before it spectacularly did.
It started innocently enough: a seemingly innocuous permission tweak in their ClickHouse database subtly changed a query’s output for the Bot Management “feature file” - a JSON payload of ~60 ML features for bot scoring. Instead, it spat out over 200 rows with duplicates, bloating the file to twice its size.
This oversized payload rippled across the edge network via a Rust-based ETL job. The code, assuming bounded input, preallocated memory accordingly but hit the limit during feature appending.
A critical unwrap() on the Result panicked the process, causing out-of-memory kills on proxy nodes. The core proxy (FL/FL2) failed to route traffic, bot scores defaulted to zero triggering false positives in blocking rules, and the network overloaded as recovery surged demand.
Initially misdiagnosed as a DDoS attack which only worsened the chaos as the status page itself glitched, Cloudflare’s teams swiftly halted the faulty feature file’s propagation and reverted to a prior stable version by 14:30 UTC. This restored most services, with full normalcy returning at 17:06 UTC.
What’s truly impressive? Rust lived up to its promise, panicking loudly and immediately rather than limping on with garbled bot scores. No sneaky OOM kills or muffled failures; the logs screamed the problem in neon.
Cloudflare’s postmortem is a masterclass in transparency, candidly owning the “latent bug” dormant since their Rust rewrite.
They’re now enforcing Clippy lints to banish unwrap()`s, treating config changes like untrusted input with rigorous validation, and rolling out staged deploys to catch issues early.
RUST CHALLENGE 🦀
Last week we had you solve the Log Analyzer parsing challenge. Good job Mike Cluck. Now, on to this week’s challenge.
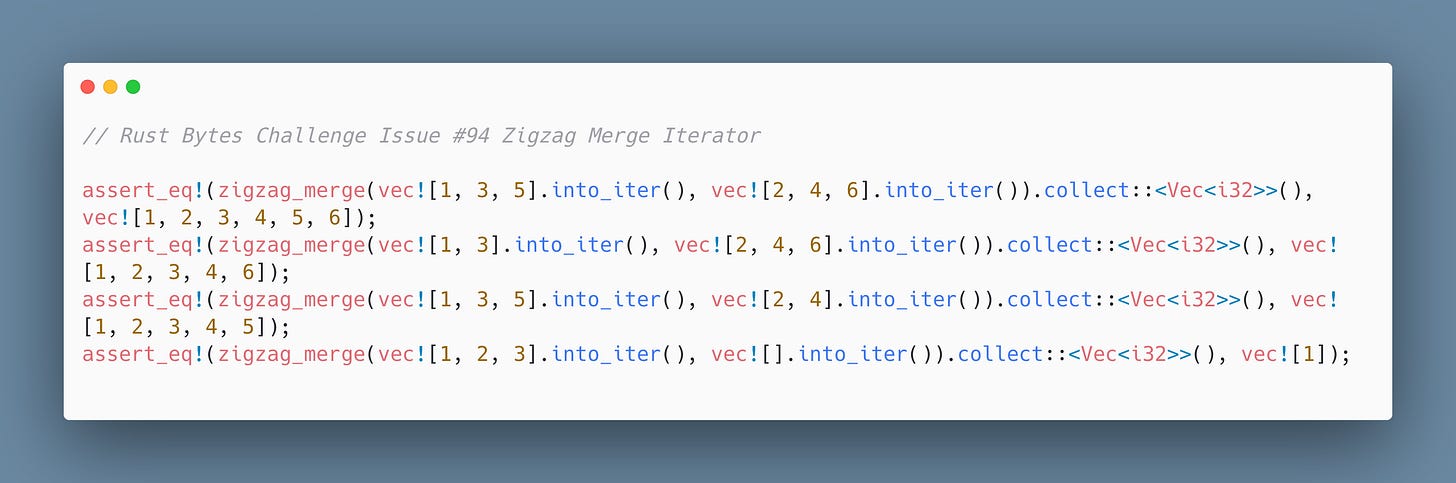
Zigzag Merge Iterator
Implement an iterator that merges two input iterators of i32 by alternating yields (first from iter1, then iter2, etc.) until both are exhausted.
If one ends early, continue with the remaining from the other.
Test your solution on Rust Playground. Once completed, please share your solution and tag us either on X, BlueSky, Mastodon, LinkedIn, or reply to this email.
PROJECT SPOTLIGHT 💡
Sprout
Sprout is a programmable UEFI bootloader written in Rust.
Linux bootloaders love stuffing logic into configs that are basically full-blown programs.
That’s great if you enjoy debugging boot failures caused by a stray space, but a nightmare if you’re injecting your own hypervisor or maintaining systems you don’t fully control.
Edera needed something machine-readable, predictable, and maintainable… so they built it.
Sprout treats boot data like, well, data. It loads configurations from TOML, keeps unsafe Rust usage minimal, and works across x86_64 and ARM64 systems.
Why Sprout’s Worth Paying Attention To
Config you can read - You can define entries, actions, and drivers in plain TOML.
Linux and Windows boot support that doesn’t fight you - EFI stub, chainloading, and initrds are handled cleanly.
Autoconfiguration that actually helps - It can generate entries from your EFI environment or BLS-compatible filesystems.
Sprout’s still young, but it’s already positioning itself as the “bootloader that won’t gaslight you.” Developers deserve that.
It’s available on GitHub at https://github.com/edera-dev/sprout.
AWESOME LINKS OF THE WEEK 🔗
It’s that time of the year again and the Rust Survey team launched the 2025 State of Rust Survey. Also Google Summer of Code 2025 results are out and rustc will use its own “v0” mangling scheme by default on nightly versions instead of the previous default, which re-used C++’s mangling scheme, starting in nightly-2025-11-21.
Brimstone is yet another JavaScript engine written from scratch in Rust, targeting full ES2025 compliance with over 97% of the ECMAScript specification already implemented.
On Netstack.FM podcast, NLnet Labs’ Terts and Arya discuss DNSSEC infrastructure, Rotonda project, Roto scripting, zero-copy optimizations, and building resilient open-source networking tools. [audio]
Nadrieril’s Truly First-Class Custom Smart Pointers discusses extending Rust’s borrow checker with place-based traits for owning references and custom pointers ideal for designing advanced, ergonomic data structures like SoA layouts.
A recently submitted GCC patch proposes adding support for Wild, the fast linker written in Rust rivaling veterans like Mold and lld.
Nick Fitzgerald wrote on the Bytecode Alliance blog about Cranelift’s new inliner, showing how heuristics, IR optimizations, and careful engineering deliver faster WebAssembly execution. Great insight into real Rust-adjacent compiler internals.
Kiran’s “Humanity is stained by the sins of C and no LLM can rewrite them away to Rust”provides a sharp critique of C-to-Rust transpilation, explaining why safety, semantics, and legacy design mismatches make automatic rewrites impossible without deep architectural reconsideration.
Julian Wood and Darko Mesaros from Amazon wrote a tutorial on Building serverless applications with Rust on AWS Lambda.
“Match it again Sam” by Anderson-Morrison walks through building a structural regex engine in Rust, revealing practical design constraints, parser architecture decisions, and lessons from implementing a nontrivial text-processing tool.
Matthew Leach open-sourced Moss, a Rust-based Linux-compatible kernel. It’s fully Linux ABI compatible, capable of running existing userspace programs while aiming to mirror the standard syscall layer.
CodeCrafters: Become a Better Rust Engineer
CodeCrafters created amazing Rust courses that push your skills beyond the basics.
You’ll have fun building real-world projects from scratch, including Git, Docker, Redis, Kafka, SQLite, Grep, BitTorrent, HTTP Server, an Interpreter, and DNS.
The courses are self-paced, so you can learn at your own speed.
Join for free and get 40% off when you upgrade. [affiliate]
SUPPORT RUST BYTES
You’re Rust Bytes’ biggest fans, and we love to see it.
Here’s how you can help:
❤️ Recommend Rust Bytes to your friends.
🤳 Connect with us on our socials: X, BlueSky, Mastodon, LinkedIn.
☕️ Buy our editors a coffee.
📨 Email us at rustaceanseditors@gmail.com for sponsorship, feedback or ideas.
I finally caught up with a long-time friend after ages. Call your friends and relive those weird, hilarious stories together.
That's all for now, Rustaceans.
John & Elley.