Rust Gets Tail Calls 🦀
Today’s Issue: Lessons Learned From Rewriting UltraGraph, Implementing a Lock-Free Channel in Rust, and Const Trait Counterexamples
Hello, Rustaceans!
As we wrap up August, I hope you make this final week a success. Let’s learn!
In this issue, we’ll discuss the Tail Call Optimization (TCO) feature currently in nightly, present you a Q/A interview, spotlight an amazing Rust project, and share ten (10) incredible links of the week.
Here’s issue 81 for you!
MAIN NEWS
Rust Gets Tail Calls 🦀
If there's one conference you shouldn't miss as a Rustacean, it's RustConf, happening this year in Seattle from September 2–5, and available online for free if you're unable to attend in person.
One talk I'm especially looking forward to is “Rust at the Last Mile in Healthcare” by Ally Salim Jr.
And speaking of exciting developments, there's also great news on the language evolution front. Rust nightly recently shipped support for become keyword and explicit tail call codegen for the LLVM backend.
Tail Call Optimization (TCO) is especially promising for interpreter writers or anyone writing recursive algorithms that don’t want to nuke memory.
So, what exactly is TCO? Think of TCO as the process by which a smart compiler can make a call to a function and take no additional stack space. When a function’s last act is calling another function (or itself), TCO ensures it reuses the current stack frame instead of piling on the stack. Picture a function a calling b, where b takes over and returns directly to a’s caller.
The become keyword makes this explicit, so you’re not gambling on the compiler’s mood swings.
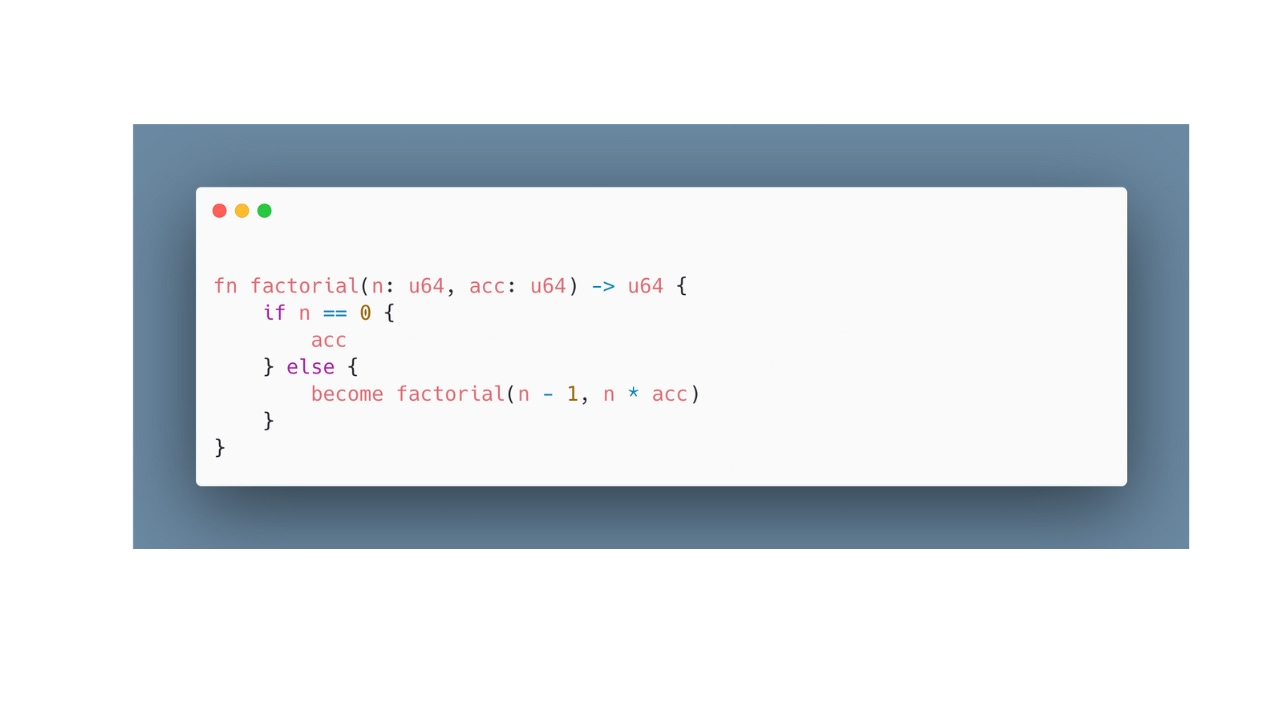
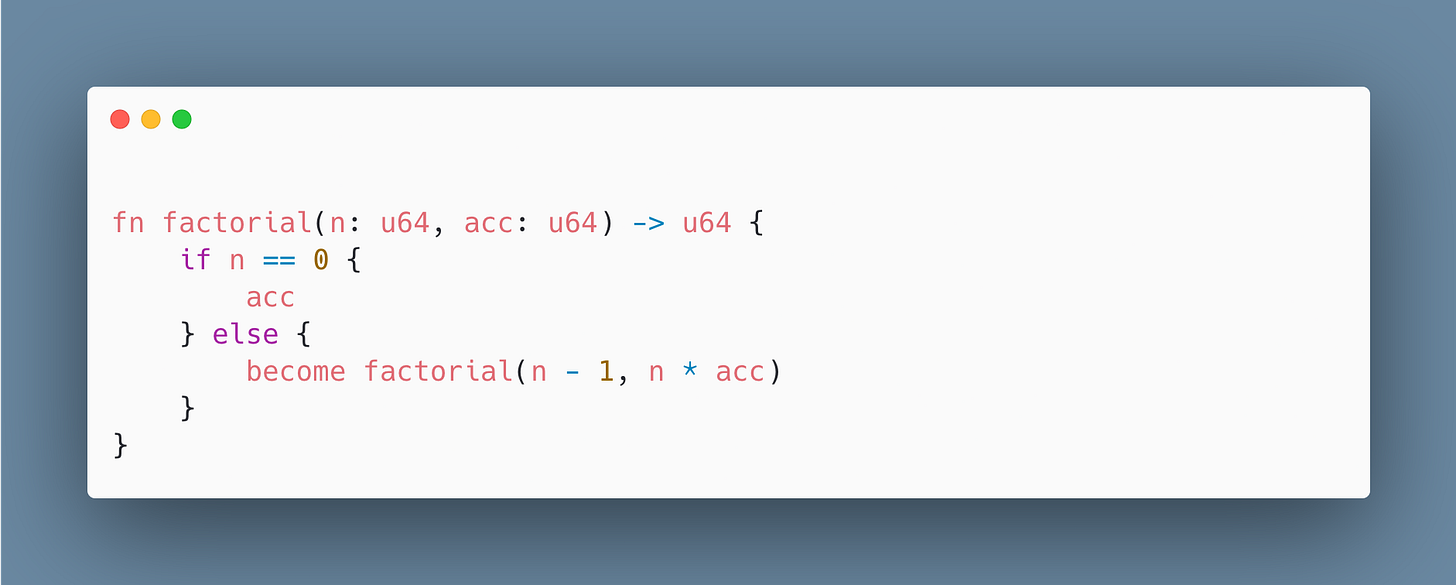
Below is a simple snippet to show TCO in action:
Note in the code snippet and in particular the factorial function uses become to tail-call itself, keeping stack usage constant.
Naturally, the question that often comes up is why not let the compiler figure it out? Isn’t that its whole job? Well, in Rust, being explicit is key. Rust wants you to opt-in. That way, when become can’t be honored, you get a compile-time error and not a panic. Pretty awesome right?
So is this a good move? Honestly, yeah. Rust’s strictness forces you to be intentional, unlike languages that might silently skip optimization or worse let your app crash. It’s a power move for performance and safety sticklers alike. Plus, it’s a nod to Rust’s “you got this, but I’m watching” vibe.
Also note that TCO is still not ready for production and has some known bugs and issues, so tread carefully until this feature will be stabilized.
In conclusion TCO lets you write recursion without blowing your stack, by ensuring your function calls itself in a tail position explicitly.
Further Reading:
RUST Q/A INTERVIEW 🦀
Q: What excites you most about Rust’s future in the next 5 years?
A: “This might be a bit out of left field, but I've been having a lot of fun with Bevy lately, so I'm happy to see where that's going (and the rest of the Rust gamedev scene).
It's also nice that async traits are finally getting out of the dyn-macro limbo that they were stuck in for so long!”
Q: What’s one feature you’d love to see added to Rust soon?
A: “Dyn traits have always been kind of a second-class citizen.. They've, of course, been there since 1.0.. but there's always been this awkward set of restrictions around what they can do (in particular, the lack of associated types!) that meant you either had to restrict your trait impls to dyn-friendly code, or write a bunch of awkward adapter code every time. So dynosaur is a really encouraging (IMO) step towards having dyn Just Work™️ when you need it in more cases, without having to pay the "dyn cost" when you don't (unlike the olden days of async_trait)”
About the Respondent: Natalie Klestrup Röijezon is one of those weird "software engineers". In her free time she works on FlickBoard, a weird keyboard for Android. For work she wrangles Kubernetes into doing things it doesn't really want to.
Connect with Natalie: Mastodon, Blog, GitHub.
PROJECT SPOTLIGHT 💡
Verus
Verus is a tool for verifying the correctness of code written in Rust. Developers write specifications of what their code should do, and Verus statically checks that the executable Rust code will always satisfy the specifications for all possible executions of the code.
It tackles one of the biggest headaches in low-level programming: trusting that your code won’t betray you at runtime.
Rather than adding run-time checks, Verus instead relies on powerful solvers to prove the code is correct.
Why Verus is actually pretty good:
Write specs directly in Rust-like syntax and let the solver do the heavy-lifting for you.
Static guarantees, no runtime hit - Verus proves properties at compile time, so there’s zero performance hit at runtime.
Goes where Rust won’t - It handles tricky stuff like raw pointers and termination checking.
Backed by research & real-world use - Verus is actively used in academic and industry projects.
Though Verus is still in active development, it is a highly promising project and is available on GitHub at https://github.com/verus-lang/verus.
AWESOME LINKS OF THE WEEK 🔗
Jake Goulding on behalf of the Infrastructure team are Demoting x86_64-apple-darwin to Tier 2 with host tools, and the leadership council are Electing new Project Directors 2025.
Tweede golf team released an Update on their advocacy for memory-safe technology to reduce vulnerabilities, align with the European Cyber Resilience Act, and promote secure-by-design software development.
Drew from Filtra interviewed Mikayla Maki, a Software Engineer at Zed Industries, they discussed Zed’s company culture, unique hiring practices, problem-solving approaches, and the development of Zed.
Aram Drevekenin wrote about the development of Zellij’s web client, explaining how a single web server per machine uses websockets and a custom URL scheme to enable browser-based access to persistent terminal sessions, complete with a secure authentication model.
Beef (Project group lead for Rust's const traits) wrote about the complexities and design considerations of stabilizing const traits, with counterarguments to alternative proposals like implicit const bounds, and syntax choices.
The amazing Rustaceans at Databend wrote about Implementing a Lock-Free Channel in Rust for Databend’s Query Pipeline.
Jyn laments about the complexity of learning Rust due to its interwoven core concepts like first-class functions, generics, references, and the borrow checker, which make it challenging to understand non-trivial programs.
DeepCausality team wrote about the Lessons they learned from Rewriting UltraGraph in Rust.
Joseph Kain authored refactoring of a Rust-based debugger to support multiple breakpoints, transitioning from a C-style implementation with global state to a more idiomatic Rust design.
Steve Pryde’s “Testing failure modes using error injection”, explains how to test failure scenarios using error injection by building a reusable mechanism to simulate and control upload failures in unit tests.
CodeCrafters: Become a Better Rust Engineer
CodeCrafters created amazing Rust courses that push your skills beyond the basics.
You’ll have fun building real-world projects from scratch, including Git, Docker, Redis, Kafka, SQLite, Grep, BitTorrent, HTTP Server, an Interpreter, and DNS.
The courses are self-paced, so you can learn at your own speed. If you’re itching to level up your Rust skills, these courses are perfect for you.
Join for free and get 40% off when you upgrade. [affiliate]
SUPPORT RUST BYTES
You’re Rust Bytes’ biggest fans, and we love to see it.
Here’s how you can help spread the word:
❤️ Recommend Rust Bytes to your friends.
🤳 Connect with us on our socials: X, BlueSky, Mastodon, Publication.
☕️ Support our editors by buying us coffee.
📨 Email us at rustaceanseditors@gmail.com for sponsorship, feedback or ideas.
I met new friends last week and had good discussions too. Stay hydrated!
That's all for now, Rustaceans.
John & Elley.