🦀 Rust-Proofing Android
Today’s issue: Gay Rust Quizes, Meta Open-Sources Below, and Surprising Rust Facts You Probably Didn’t Know
Hello, Rustaceans
In this issue, we’ll highlight Google’s Rust-in-Android progress report, present you a challenge, spotlight an amazing project, and share 10 incredible links of the week.
Here’s issue 93 for you!
MAIN NEWS
Rust-Proofing Android
Last week, Google released a progress report on Rust in the Android codebase and yes, the numbers are as wild as the hype.
Four years since Rust’s Android adoption, the numbers don’t lie: a 1000x drop in memory-safety vulnerabilities and a 0.2 bugs per million lines of Rust. Meanwhile, they found that C/C++ is still clocking in at ~1,000 bugs per 1MLOC and buffer overflows are still fashionable.
But the best part? Rust didn’t just make Android safer, it also made engineers faster. Google’s data shows Rust changes spend 25% less time in code review and see 4x fewer rollbacks compared to C/C++. Translating to: Rust prevents your PR from becoming a week-long group therapy session.
And Google is leaning in hard with their other tools. PNG parsers? Rust. JSON? Rust. Web fonts? Rust again. Even firmware is getting the Rust spa treatment, because apparently once you taste memory safety, you start rewriting everything that ever wronged you.
Rust’s adoption curve inside Google resembles a startup growth graph drawn by someone who’s had too much cold brew.
Of course, no honeymoon is perfect. Google did have a rough moment with what they dramatically titled their “First Rust Memory Safety Vulnerability… Almost.” The culprit lived in unsafe Rust, aka the part of the language everyone loves to fearmonger about, but it got caught before hitting production.
The guardrails did their job, Scudo amplified the alarms, and the whole incident became a free training module instead of a screaming-on-Twitter CVE fiasco. Google even open-sourced fresh unsafe-review materials because nothing says “we’re confident” like airing your safety homework.
What’s wild is watching a company that literally makes its own languages go full stan-mode for Rust. You know it’s real when Google, the house of Go, starts saying “yeah Rust might actually be the move.”
At this rate, Android might need a new slogan: “Powered by Rust and powered correctly this time.”
RUST CHALLENGE 🦀
Last week we had you solve the Grouped by Frequency challenge. Great solutions from Marius ₿, Ype Kingma, Atul, and Andreas Grois. Now, on to this week’s challenge.
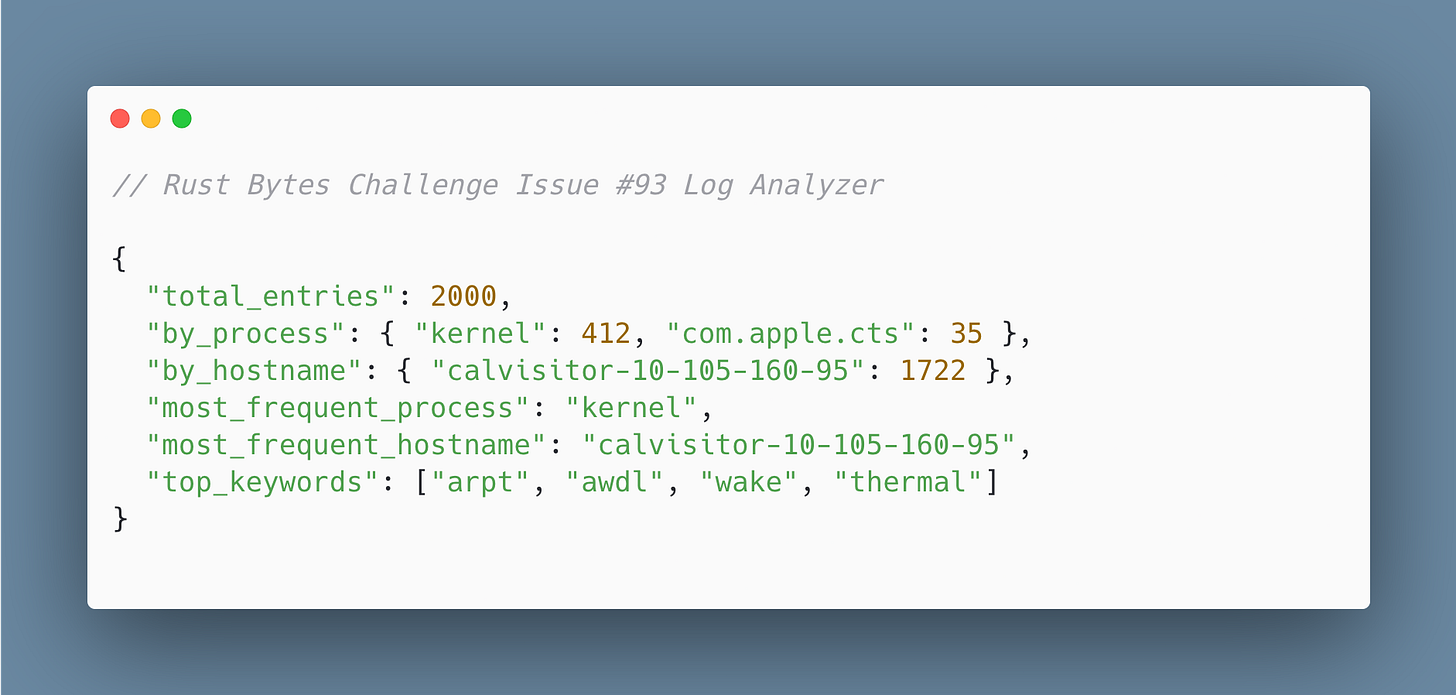
Log Analyzer
You are given a system log file named Mac_2k.log, located in the src directory.
The file contains real macOS-style log entries that follow this general pattern:
<Month> <Day> <Time> <Hostname> <Process>[PID]: <Message>Write a Rust program that reads and parses the file Mac_2k.log.
Each line should be parsed into:
timestamp - e.g.,
Jul 1 09:00:55hostname - e.g.,
calvisitor-10-105-160-95process name - e.g.,
kernel,com.apple.cts,configd, etc.process ID (PID) - e.g.,
[0],[43]log message - everything after the colon
What you need to produce
Per-process stats: Count how many log entries each process generated (process name only, ignore PID).
Per-hostname stats: Count how many entries came from each hostname.
Global stats:
Most frequent process
Most frequent hostname
Optional: Most common keywords in log messages (lowercased, tokenized, stopwords removed)
Write all results to a summary.json file in the structure sample below:
You can start by cloning the starter template on GitHub for reference.
Once completed, please share your solution and tag us either on X, BlueSky, Mastodon, LinkedIn, or reply to this email.
PROJECT SPOTLIGHT 💡
Tonic
Tonic is a Rust implementation of gRPC, a high performance, open source, general RPC framework that puts mobile and HTTP/2 first.
Built on hyper’s HTTP/2 and prost’s codegen, tonic flips the script on RPC, letting you build high-speed, bi-di streams without breaking a sweat.
It’s the toolkit for when your services need to chat like pros without fumbling with Protocol Buffers.
What seals the deal? Here’s tonic’s superpowers:
Bi-Directional Streaming - Tonic lets data flow both ways with no buffering bottlenecks in sight.
Async IO on Steroids - Powered by tokio, it handles requests faster with high performance.
Interoperability - Talks flawlessly with Go, Java, whatever – tonic’s got your cross-team handshakes covered.
Load Balancing That Doesn’t Lie - Tonic spreads the love across backends keeping your setup running even when traffic spikes.
Check out Tonic on GitHub.
AWESOME LINKS OF THE WEEK 🔗
Shortly after Rust 1.91.0 was released, the Rust Release Team shipped Rust 1.91.1 to fix two regressions introduced in 1.91.0.
Rustaceans at Meta open-sourced Below, a time-traveling resource monitor for modern Linux systems - htop, watch out.
Niko Matsakis wrote Just Call Clone (or Alias), proposing a way to make working with
Cloneand the newAliastrait more ergonomic, particularly in closures and async contexts.Unfair Rust Quiz is a collection of extremely hard and sometimes even unfair questions about Rust, made by the gayest people you know.
Rust’s println!() and related macros are now faster and produce smaller binaries thanks to Mara’s fmt::Arguments rewrite. The changes are set to arrive in Rust 1.93.0, expected in January 2026.
The Lanczos algorithm is fast but a memory hoarder; running it in a two-pass mode cuts gigabytes of storage and can even boost performance via better caching.
Christian Legnitto did an interview with the Rust Foundation about Rust on the GPU. [video]
Andrew Lilley Brinker wrote “Memory Safety for Skeptics” arguing that memory-safe languages prevent bugs better. He pushes a pragmatic path - write new code in safe languages, wrap or isolate old C/C++, and rewrite only the riskiest parts.
Rust hiring is surging: more openings, wider industry adoption, and rising demand for senior engineers, according to Filtra’s October jobs report.
Evis Drenova wrote about building a Rust autograd system from scratch, covering tensors, computational graphs, forward/backward passes, gradients, ReLU, and a neural network.
Bonus:
Keynote: Rust in the Linux Kernel, Why? - Greg Kroah-Hartman
We released “did-you-know?”, a collection of fun facts about Rust you probably didn’t know.
CodeCrafters: Become a Better Rust Engineer
CodeCrafters created amazing Rust courses that push your skills beyond the basics.
You’ll have fun building real-world projects from scratch, including Git, Docker, Redis, Kafka, SQLite, Grep, BitTorrent, HTTP Server, an Interpreter, and DNS.
The courses are self-paced, so you can learn at your own speed.
Join for free and get 40% off when you upgrade. [affiliate]
SUPPORT RUST BYTES
You’re Rust Bytes’ biggest fans, and we love to see it.
Here’s how you can help:
❤️ Recommend Rust Bytes to your friends.
🤳 Connect with us on our socials: X, BlueSky, Mastodon, LinkedIn.
☕️ Buy our editors a coffee.
📨 Email us at rustaceanseditors@gmail.com for sponsorship, feedback or ideas.
This week I have been feeling lazy and also got some time to watch some movies.
That's all for now, Rustaceans.
John & Elley.