🦀 Rust’s First Linux CVE
Today’s Issue: Microsoft Goes All-In on Rust, Cargo Gets a Supposed “Drop-In Replacement,” and Rust’s Parenting Rue.
Hello, Rustaceans
Hope you had an amazing Christmas last week. Wishing you a happy New Year ahead - let’s boogie!
In this issue, we’ll discuss the recent Rust CVE that was found in Linux, present you a challenge, spotlight an amazing project, and share 10 incredible links of the week.
Here’s issue 99.
MAIN NEWS
Rust’s First Linux CVE
For years, Rust for Linux has been pitched as the solution to entire classes of kernel bugs, use-after-free, null pointer derefs, and memory corruption. So when news broke that CVE-2025-68260, a security vulnerability had slipped through Rust code inside the Linux kernel, the reaction was… loud.
The vulnerability resided in the Rust-based rewrite of Android’s Binder driver (`rust_binder`), a critical inter-process communication (IPC) mechanism that enables Android apps to securely exchange data. Introduced in Linux 6.18, this driver handles complex tasks like death notifications, alerting processes when a Binder node is destroyed.
The bug is a race condition involving an intrusive linked list called `death_list`. The problematic pattern works like this: a lock is acquired to drain all pending death notifications from the shared `death_list` into a temporary local list. The lock is then released, allowing the function to process (and free) those notifications without holding the lock for too long. However, during this unlocked processing phase, a concurrent thread can perform an unsafe removal of an element still referenced in the local list. This violates the safety comment on the `unsafe` removal operation, which assumed no parallel modifications to the list pointers.
The result? Corruption of the prev/next pointers in the intrusive list, leading to invalid memory accesses, kernel oops, and ultimately a system panic — a classic denial-of-service (DoS) scenario. Symptoms included errors like “Unable to handle kernel paging request,” confirming pointer corruption rather than a more exploitable flaw.
Importantly, this is a crash-only bug as it causes a denial of service but offers no demonstrated path to privilege escalation or remote code execution, unlike many historical Binder vulnerabilities in the C implementation.
Exposure is limited: the issue only affects kernels where the Rust Binder driver is explicitly enabled (via config options like `CONFIG_ANDROID_BINDER_IPC_RUST`) and selected at runtime, primarily Android-focused builds or custom configurations.
The fix, already backported to stable releases, rewrites the release logic to process notifications directly under the lock or avoids the intermediate list entirely, eliminating the race window.
Lessons from the rubble? First, Rust’s your seatbelt, not your autopilot, especially in `unsafe` zones where you’re borrowing C’s chaos. Second, test those lock-drop dances like your deploy depends on it.
RUST CHALLENGE 🦀
Last week we you solve the Graph Gossip challenge. LGTM jancha. Now onto this weeks challenge.
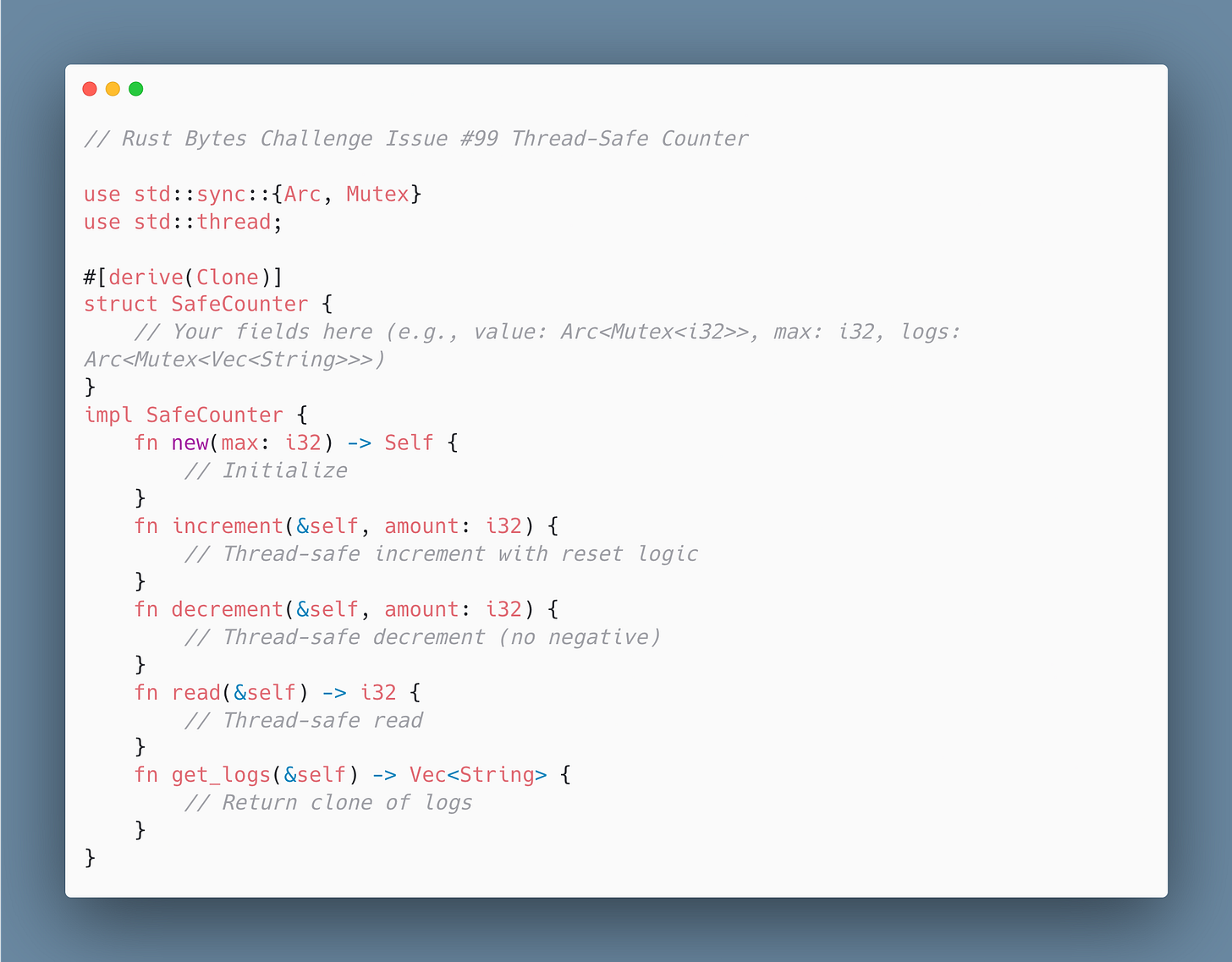
Thread-Safe Counter
Implement a thread-safe counter that supports increment, decrement, and read operations.
Use Rust’s concurrency primitives (e.g., Arc, Mutex) to ensure safety across multiple threads. Add a creative twist: The counter resets to zero if it exceeds a configurable max value, and logs resets (simulate logging with a shared vector).
Test your solution on Rust Playground. Once completed, please share your solution and tag us either on X, BlueSky, Mastodon, LinkedIn, or reply to this email.
PROJECT SPOTLIGHT 💡
Salsa
Salsa is a generic framework for on-demand, incrementalized computation.
Born from the brains behind adapton, glimmer, and Rustc’s query, it’s your ticket to on-demand, incremental computation without the full-system freakouts.
Salsa models your whole shebang as queries: raw inputs you swap at will, and pure functions that spit out values only when needed. It memos the heck out of results, then smartly invalidates and re-runs just the affected bits.
Features that make Salsa amazing:
Query Magic - Slap a macro on your fn, and boom – it’s tracked, memoized, and cycle-proof. Change an input? It ripples precisely.
Zero-Boilerplate Inputs - Define your data sources once, tweak ‘em freely. Salsa handles the versioning so you don’t have to babysit diffs.
Cycle Shenanigans - Spots loops in your deps and recovers gracefully, calling your fix-it fn every iteration. Because infinite recursion is so last decade.
Salsa is open-source and available on GitHub at https://github.com/salsa-rs/salsa.
AWESOME LINKS OF THE WEEK 🔗
The Rust program’s end-of-2025 management update and December Project Director update are out. The Goals team is now accepting proposals for 2026 project goals, submit yours soon.
Mullvad VPN released GotaTun, a Rust-based WireGuard fork replacing crash-prone wireguard-go; Android rollout yields zero crashes, faster speeds, and lower battery use.
Ralf Jung, the Miri team lead, wrote about Miri’s latest updates, which include a POPL 2026 paper and advancements in shims, diagnostics, concurrency, optimizations, and native code support.
Hurry is a drop-in replacement for Cargo that automatically caches dependencies with zero setup, because waiting on builds in 2025 is a personality flaw.
Yoshua Wuyts proposes a “throws” keyword for Rust’s fallibility effect, inspired by Swift, to annotate fallible functions, blocks, and closures with concrete error types, replacing yeet with throw and omitting try.
Steve Klabnik (yes, that Steve - co-author of The Rust Book) released Rue: a hobby systems language chasing GC-free memory safety, but with ergonomics that don’t make you fight the compiler for basic happiness.
Glen interviews Thomas Eizinger on Firezone, a Rust/Elixir-based zero-trust VPN using WireGuard for secure, performant enterprise access. [audio]
Jorge Ortiz-Fuentes wrote Rust unit testing: basic HTTP testing, a hands-on guide to unit testing Axum-based HTTP servers without any network involvement.
In other news: Microsoft is going all-in on Rust. They’ve got a research team poking at AI-assisted migrations from C/C++ codebases to Rust.
The Algebra of Loans in Rust explains extending Rust’s borrow checker with new reference types (&own, &uninit, pinning variants) via detailed loan interaction tables.
CodeCrafters: Become a Better Rust Engineer
CodeCrafters created amazing Rust courses that push your skills beyond the basics.
You’ll have fun building real-world projects from scratch, including Git, Docker, Redis, Kafka, SQLite, Grep, BitTorrent, HTTP Server, an Interpreter, and DNS.
The courses are self-paced, so you can learn at your own speed.
Join for free and get 40% off when you upgrade. [affiliate]
SUPPORT RUST BYTES
You’re Rust Bytes’ biggest fans, and we love to see it.
Here’s how you can help:
❤️ Recommend Rust Bytes to your friends.
🤳 Connect with us on our socials: X, BlueSky, Mastodon, LinkedIn.
☕️ Buy our editors coffee.
📨 Email us at rustaceanseditors@gmail.com for sponsorship, feedback or ideas.
Had a blast last week with friends and family. Wishing you a happy new year ahead.
That's all for now, Rustaceans.
John & Elley.